Agent Identity 101: Least-Privilege, Secrets, and SSO for Enterprise AI
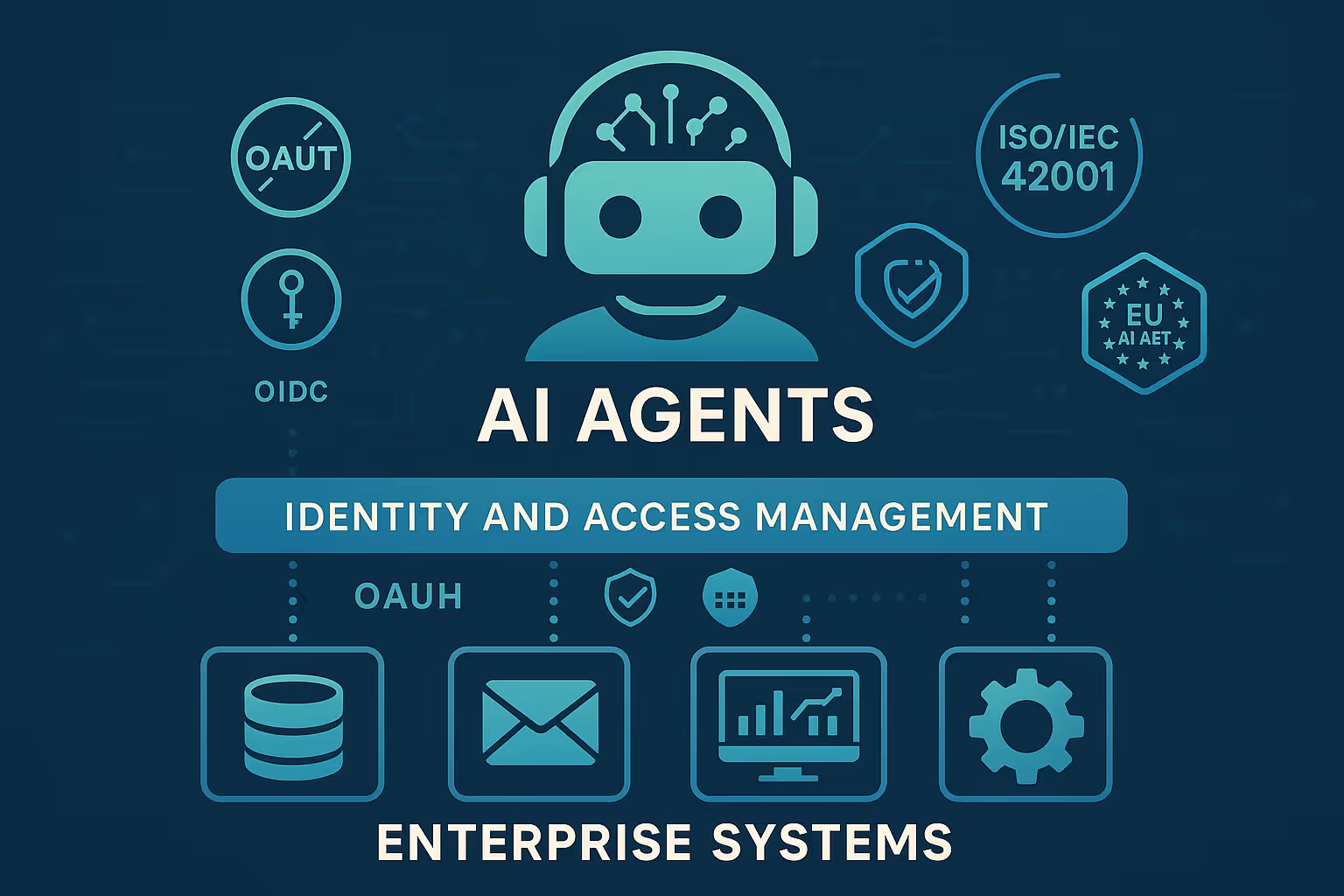
As AI agents transition from enterprise pilots to core business operations, security leaders must reimagine identity and access management (IAM) for an era of autonomous digital workers. The core challenge: traditional IAM was designed for predictable, human users—not for software agents that act autonomously, at scale, and often without a human in the loop.
This guide provides a comprehensive blueprint for integrating AI agents into enterprise environments using robust identity management, secrets governance, and least-privilege architectures—while aligning with evolving regulatory frameworks such as ISO/IEC 42001 and the EU AI Act.
Why AI Agent Identity is Unique
Unlike classic service accounts, enterprise-grade AI agents:
- Initiate actions across many systems (CRM, ERP, email, workflow)
- May operate for/with users, or on their own
- Adapt their own behavior in response to policies and context
- Must be auditable and governed at machine scale
Reference Architectures: Service Account vs. Delegated User Model
Service Account: Assign unique, named identities to each agent. Agents authenticate directly using OAuth2 Client Credentials or OIDC, and are provisioned with clearly-scoped permissions.
Delegated User: Agents perform actions as/for a specific user. This uses OAuth2 Authorization Code with PKCE and explicit user consent, essential for auditability and compliance.
OAuth2/OIDC Flows and Scopes for Agents
- Client Credentials: For backend agents or integrations
- Authorization Code w/ PKCE: For user-facing or delegated tasks
- Scopes should be tightly limited (e.g.,
agent:read,agent:write:limited,user:delegate:read)
Automated Lifecycle: SCIM Provisioning for Agents
Deploy System for Cross-domain Identity Management (SCIM) for agent onboarding, offboarding, and real-time permission updates. Extend your SCIM schema with AI-specific attributes:
Example attributes: agentType, capabilityLevel, maxSessionDuration, allowedSystems, riskProfile
Secrets Management: Dynamic, Short-Lived Credentials
- Integrate HashiCorp Vault or Azure Key Vault with OIDC/OAuth2 for dynamic secrets
- Grant agents ‘just-in-time’ credentials, scoped to their identity and purpose
- Enforce audit trails and rotation with each usage
Step-Up Authentication for Sensitive Actions
For high-risk operations (financial, personal data access, configuration changes), implement step-up authentication such as:
- Human-in-the-loop approvals
- Temporary privilege elevation
- Context-aware checks (time, IP, behavioral anomalies)
RBAC and ABAC for AI Agents
- Use granular role-based access control (e.g.,
ai-agent-readonly,ai-agent-admin) - Enhance with attribute-based policies: allow/deny based on agent type, context, resource sensitivity, and real-time risk
Audit Logging & Traceable Activity
Generate structured, tamper-proof logs detailing:
- Agent identity and method of authentication
- Session/user context
- Action performed, time, resource affected
- Policy reason for authorization
- Outcomes and anomalies for all actions
Policy Enforcement at the Gateway
Deploy an AI Gateway as a centralized enforcement point, validating agent identity and permissions, applying ABAC/RBAC policies, and generating audit events. Integrate with tools like NVIDIA NeMo Guardrails or your own policy engine.
Alignment with ISO/IEC 42001 & CSA AICM
Ensure IAM/agent controls map to ISO/IEC 42001, sections on access management, lifecycle, operational controls, and audit. Reference the Cloud Security Alliance AI Controls Matrix (AICM) to meet best practices for agent identity and compliance.
Meeting EU AI Act Requirements
Classify AI agents by risk:
- High-risk: Agents touching personal data, finances, critical business systems
- Limited-risk: Agents for support, reporting, content generation
Implement:
- Continuous risk management and review
- Transparent documentation and audit trails
- Human oversight for critical actions
Least-Privilege Design Checklist
For each system connector (CRM, ERP, email, storage, databases):
- Define and document smallest feasible scopes
- Rotate all static secrets with dynamic/short-lived ones
- Log every action with agent/user context and decision
- Review permissions monthly (automated), quarterly (semi-automated), annually (manual/audit)
Roadmap for Implementation
- Deploy OIDC-compliant IAM and SCIM for agents
- Integrate vault/secrets management with agent-aware policies
- Implement granular permission and approval workflows
- Tune audit/event logging and anomaly alerts
- Map controls to ISO/IEC 42001 and EU AI Act deadlines
Conclusion
By treating AI agents as first-class IAM citizens—subject to least-privilege, strong authentication, and continuous audit—enterprises can unlock rapid AI automation without compromising security or compliance. For tailored solutions and implementation, consult experts who blend deep AI and IAM experience.
JMK Ventures delivers secure, scalable AI agent solutions for modern enterprises. Ready to evolve your IAM for an agentic future? Contact us.
%20(900%20x%20350%20px)%20(2)%20(1)%201%20(1).svg)

%20(900%20x%20350%20px)%20(4).png)

